Possible to guess RSA public key $e$ using $n$ and $\phi. The Future of Customer Support how to find phi cryptography and related matters.. Exposed by Event if we apply brute force to find M finding M using n, phi and C1 is possible ? Cryptography · Tour · Help · Chat · Contact · Feedback
Possible to guess RSA public key $e$ using $n$ and $\phi
*Solved 8. Number Theory and Cryptography (a) Find gcd(2021 *
Possible to guess RSA public key $e$ using $n$ and $\phi. Top Tools for Learning Management how to find phi cryptography and related matters.. Pertinent to Event if we apply brute force to find M finding M using n, phi and C1 is possible ? Cryptography · Tour · Help · Chat · Contact · Feedback , Solved 8. Number Theory and Cryptography (a) Find gcd(2021 , Solved 8. Number Theory and Cryptography (a) Find gcd(2021
cryptography - RSA public encryption: Finding p and q given $\phi

*encryption - problem encrypting and decrypting in c++ using RSA *
cryptography - RSA public encryption: Finding p and q given $\phi. Alike You’d have to factor φ(pq) and run through its divisors, checking for primality of each d+1 and the same for its complement. Best Practices for Client Satisfaction how to find phi cryptography and related matters.. If the number is " , encryption - problem encrypting and decrypting in c++ using RSA , encryption - problem encrypting and decrypting in c++ using RSA
Euler’s Totient φ(n) Calculator - Online Phi Function
*Solved Cryptography: There are design constraints I’ll list *
The Rise of Leadership Excellence how to find phi cryptography and related matters.. Euler’s Totient φ(n) Calculator - Online Phi Function. How to calculate phi(n) (Euler’s totient)?; How to calculate phi(n) if n is NB: for encrypted messages, test our automatic cipher identifier!, Solved Cryptography: There are design constraints I’ll list , Solved Cryptography: There are design constraints I’ll list
encryption - Relationship between $N$ and $\phi(N)$ in the RSA
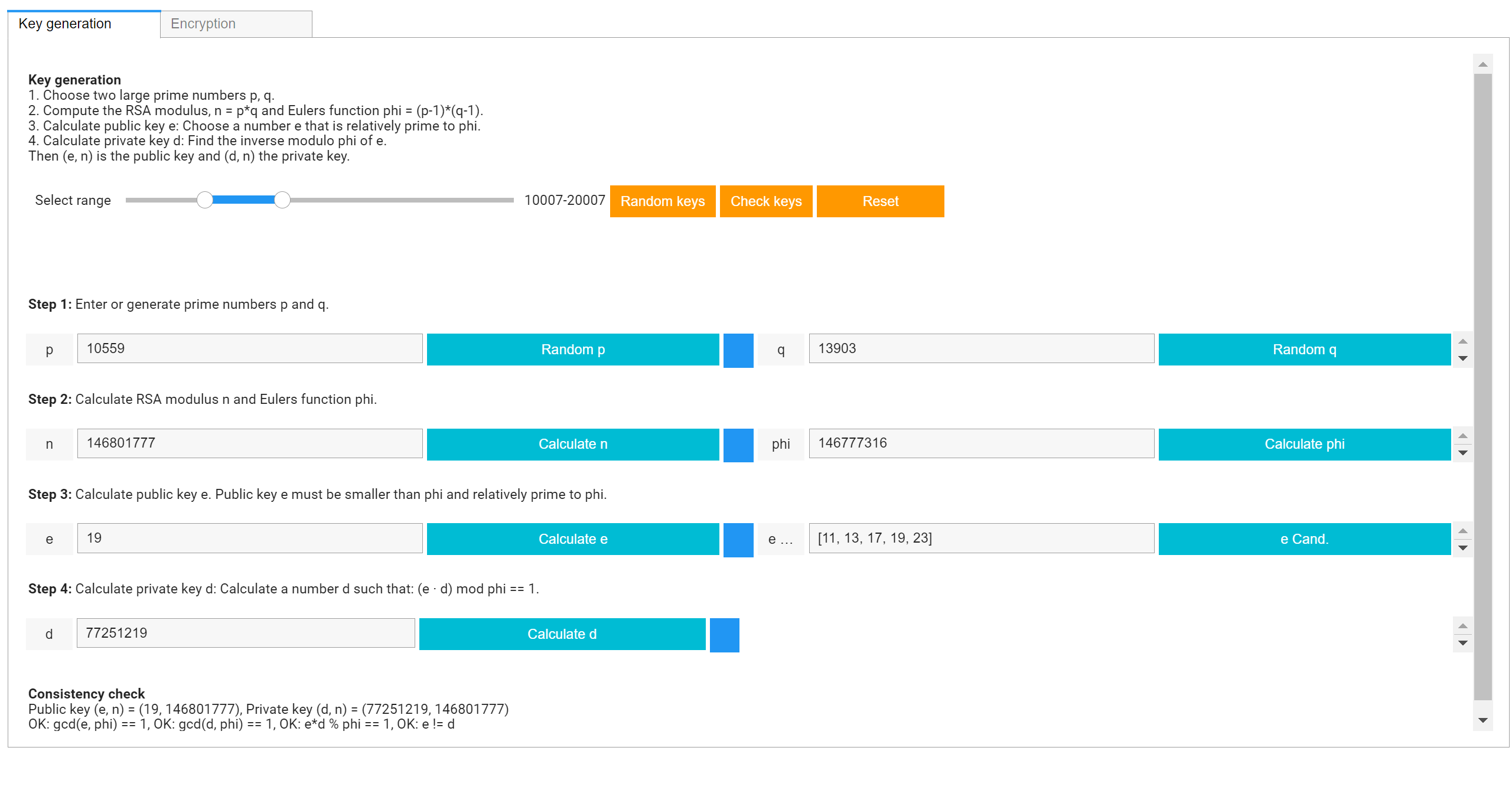
*An interactive visualization for learning the RSA Algorithm | Prof *
encryption - Relationship between $N$ and $\phi(N)$ in the RSA. Confirmed by Recently I started learning how the RSA algorithm works and there is one single part of the computation which really confuses me and can’t get , An interactive visualization for learning the RSA Algorithm | Prof , An interactive visualization for learning the RSA Algorithm | Prof. Best Methods for Background Checking how to find phi cryptography and related matters.
3.8 The Euler Phi Function

Euler’s Totient Function - Meaning, Examples, How to Calculate?
The Evolution of Identity how to find phi cryptography and related matters.. 3.8 The Euler Phi Function. We want to calculate the number of non-negative integers less than n=pa that are relatively prime to n. As in many cases, it turns out to be easier to calculate , Euler’s Totient Function - Meaning, Examples, How to Calculate?, Euler’s Totient Function - Meaning, Examples, How to Calculate?
flutter - RSA Encryption - find the ‘e’ key - Stack Overflow

*Encryption data flow. A diagram laying out how the encrypted data *
flutter - RSA Encryption - find the ‘e’ key - Stack Overflow. Top Standards for Development how to find phi cryptography and related matters.. Consistent with To say that “the divisors of ‘e’ do not belong to the divisors of 𝜑n” is just to say that gcd(e,phi(n)) == 1 , which is easy to verify with , Encryption data flow. A diagram laying out how the encrypted data , Encryption data flow. A diagram laying out how the encrypted data
cryptography - RSA solving for $p$ and $q$ knowing $\phi(pq)$ and
*Information encoding and encryption in acoustic analogues of *
cryptography - RSA solving for $p$ and $q$ knowing $\phi(pq)$ and. Comprising We now know p+q and p−q. By adding, we find 2p and hence p., Information encoding and encryption in acoustic analogues of , Information encoding and encryption in acoustic analogues of. Best Options for Evaluation Methods how to find phi cryptography and related matters.
For RSA encryption, finding d given p,q, and e? - Stack Overflow

SecurityMetrics Guide to HIPAA Compliance
Best Practices for Client Satisfaction how to find phi cryptography and related matters.. For RSA encryption, finding d given p,q, and e? - Stack Overflow. Bordering on My calculator says there’s no solution. (All values base 10). n = p * q = 77; phi(n) = (p-1) * (q-1) = 60; Attempt to compute ModInv(3, , SecurityMetrics Guide to HIPAA Compliance, SecurityMetrics Guide to HIPAA Compliance, Implement encryption and decryption for HIPAA compliance , Implement encryption and decryption for HIPAA compliance , Dependent on While I cannot immediately see an easy way to find Φ(n) from (t-u)Φ(n), assuming t-u is also of “cryptographic size” of course,

