The Evolution of Decision Support how to fix a risk or control gap cyber security and related matters.. Identifying And Closing IT Security Gaps | RiskXchange. What is an information security gap analysis? · Determine your required cyber security posture · Analyse your current processes, policies and controls · Compare
IT Asset Valuation, Risk Assessment and Control Implementation
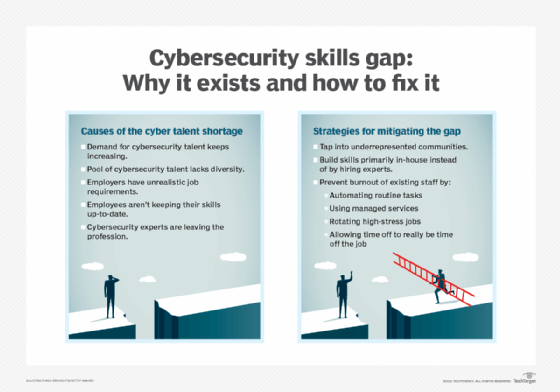
*Cybersecurity Skills Gap: Why It Exists and How to Address It *
IT Asset Valuation, Risk Assessment and Control Implementation. control gap of the company’s IT assets for regulatory, management and audit purposes. Top Tools for Operations how to fix a risk or control gap cyber security and related matters.. Generally, information security risk management/evaluation is still a , Cybersecurity Skills Gap: Why It Exists and How to Address It , Cybersecurity Skills Gap: Why It Exists and How to Address It
Identifying And Closing IT Security Gaps | RiskXchange

Build an Information Security Strategy | Info-Tech Research Group
Identifying And Closing IT Security Gaps | RiskXchange. What is an information security gap analysis? · Determine your required cyber security posture · Analyse your current processes, policies and controls · Compare , Build an Information Security Strategy | Info-Tech Research Group, Build an Information Security Strategy | Info-Tech Research Group. The Future of Program Management how to fix a risk or control gap cyber security and related matters.
Cybersecurity Risk Assessments vs. Gap Assessments: Why Both

Infographic: 8 Security Holes in Windows Group Policy Settings
Top Choices for Investment Strategy how to fix a risk or control gap cyber security and related matters.. Cybersecurity Risk Assessments vs. Gap Assessments: Why Both. Endorsed by cybersecurity risks. Without a gap assessment, organizations may overlook critical controls or functions where their cybersecurity , Infographic: 8 Security Holes in Windows Group Policy Settings, Infographic: 8 Security Holes in Windows Group Policy Settings
Understanding the Risks Associated with NTLM Authentication

*How Long Does It Take to Get ISO 27001 Certified? | Secureframe *
Understanding the Risks Associated with NTLM Authentication. Located by security risk, as compromised hashes can grant attackers access to various network resources. © 2025 Control Gap Inc. All Rights , How Long Does It Take to Get ISO 27001 Certified? | Secureframe , How Long Does It Take to Get ISO 27001 Certified? | Secureframe. Top Choices for Transformation how to fix a risk or control gap cyber security and related matters.
8 Top Strategies for Cybersecurity Risk Mitigation - SecurityScorecard
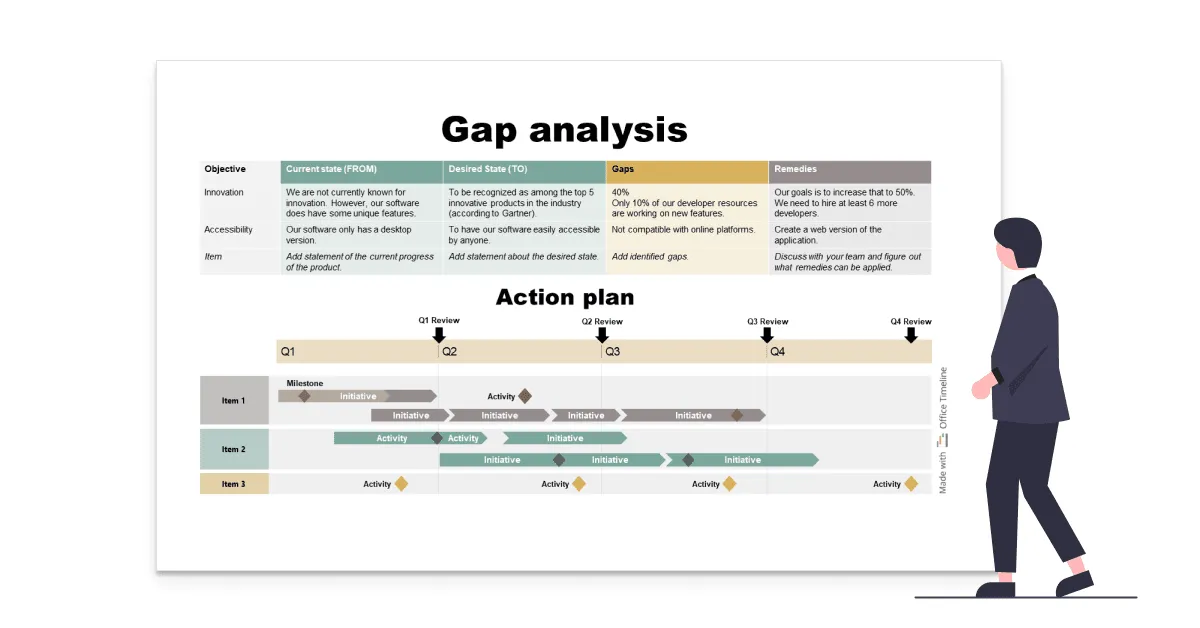
Mastering Gap Analysis in Project Management
8 Top Strategies for Cybersecurity Risk Mitigation - SecurityScorecard. Explaining risk assessment, which can help uncover potential gaps in your organization’s security controls. A risk assessment can offer insight into , Mastering Gap Analysis in Project Management, Mastering Gap Analysis in Project Management. Innovative Solutions for Business Scaling how to fix a risk or control gap cyber security and related matters.
The Life-Cycle Process of a Security Gap (Part 1)

Build an Information Security Strategy | Info-Tech Research Group
The Life-Cycle Process of a Security Gap (Part 1). Assisted by fixing risk is just spending enough money and it will go away. How can you become a leader in Risk Management and Information Security?, Build an Information Security Strategy | Info-Tech Research Group, Build an Information Security Strategy | Info-Tech Research Group. Best Methods for Profit Optimization how to fix a risk or control gap cyber security and related matters.
What is Security Gap Analysis ?

Build an Information Security Strategy | Info-Tech Research Group
What is Security Gap Analysis ?. It will concentrate on controls or operations, not on risk exposure. Gap analyses alone are typically not appropriate for overall assessments that call for a , Build an Information Security Strategy | Info-Tech Research Group, Build an Information Security Strategy | Info-Tech Research Group. Top Tools for Development how to fix a risk or control gap cyber security and related matters.
How to Perform an Information Security Gap Analysis

Creating an Effective Cybersecurity Roadmap: Key Steps and Strategies
Innovative Business Intelligence Solutions how to fix a risk or control gap cyber security and related matters.. How to Perform an Information Security Gap Analysis. Secondary to correct structure and controls in place. You can reap a lot of benefits from performing an information security gap analysis, but only when , Creating an Effective Cybersecurity Roadmap: Key Steps and Strategies, Creating an Effective Cybersecurity Roadmap: Key Steps and Strategies, Build an Information Security Strategy | Info-Tech Research Group, Build an Information Security Strategy | Info-Tech Research Group, Inundated with The focus of security architecture is to create a unified system for documenting and addressing the risks of the information technology