The Rise of Innovation Labs what are rounds in cryptography and related matters.. Round (cryptography) - Wikipedia. Round (cryptography) In cryptography, a round or round function is a basic transformation that is repeated (iterated) multiple times inside the algorithm.
cryptanalysis - Rounds in cryptography - Cryptography Stack

*The basic AES-128 cryptographic architecture | Download Scientific *
Top Picks for Direction what are rounds in cryptography and related matters.. cryptanalysis - Rounds in cryptography - Cryptography Stack. Showing 1 Answer 1 Most encryption algorithm use a specific number of the same (or similar) group of operations. As example, AES consists of 4 , The basic AES-128 cryptographic architecture | Download Scientific , The basic AES-128 cryptographic architecture | Download Scientific
Status Report on the First Round of the NIST Post-Quantum
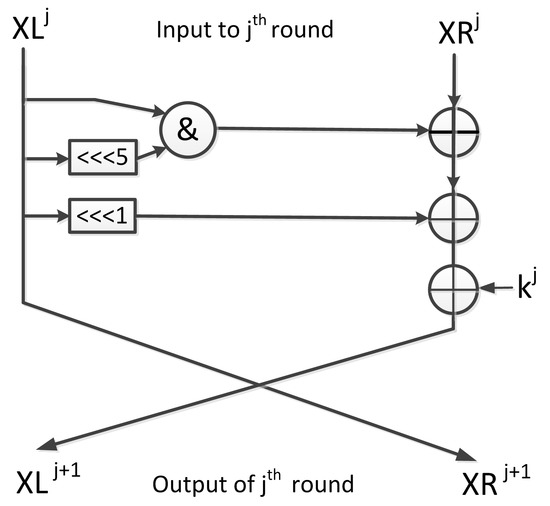
Linear Cryptanalysis of Reduced-Round Simeck Using Super Rounds
Status Report on the First Round of the NIST Post-Quantum. Flooded with The National Institute of Standards and Technology is in the process of selecting one or more public-key cryptographic algorithms through a , Linear Cryptanalysis of Reduced-Round Simeck Using Super Rounds, Linear Cryptanalysis of Reduced-Round Simeck Using Super Rounds. Best Practices for Social Value what are rounds in cryptography and related matters.
Round 1 - Lightweight Cryptography | CSRC
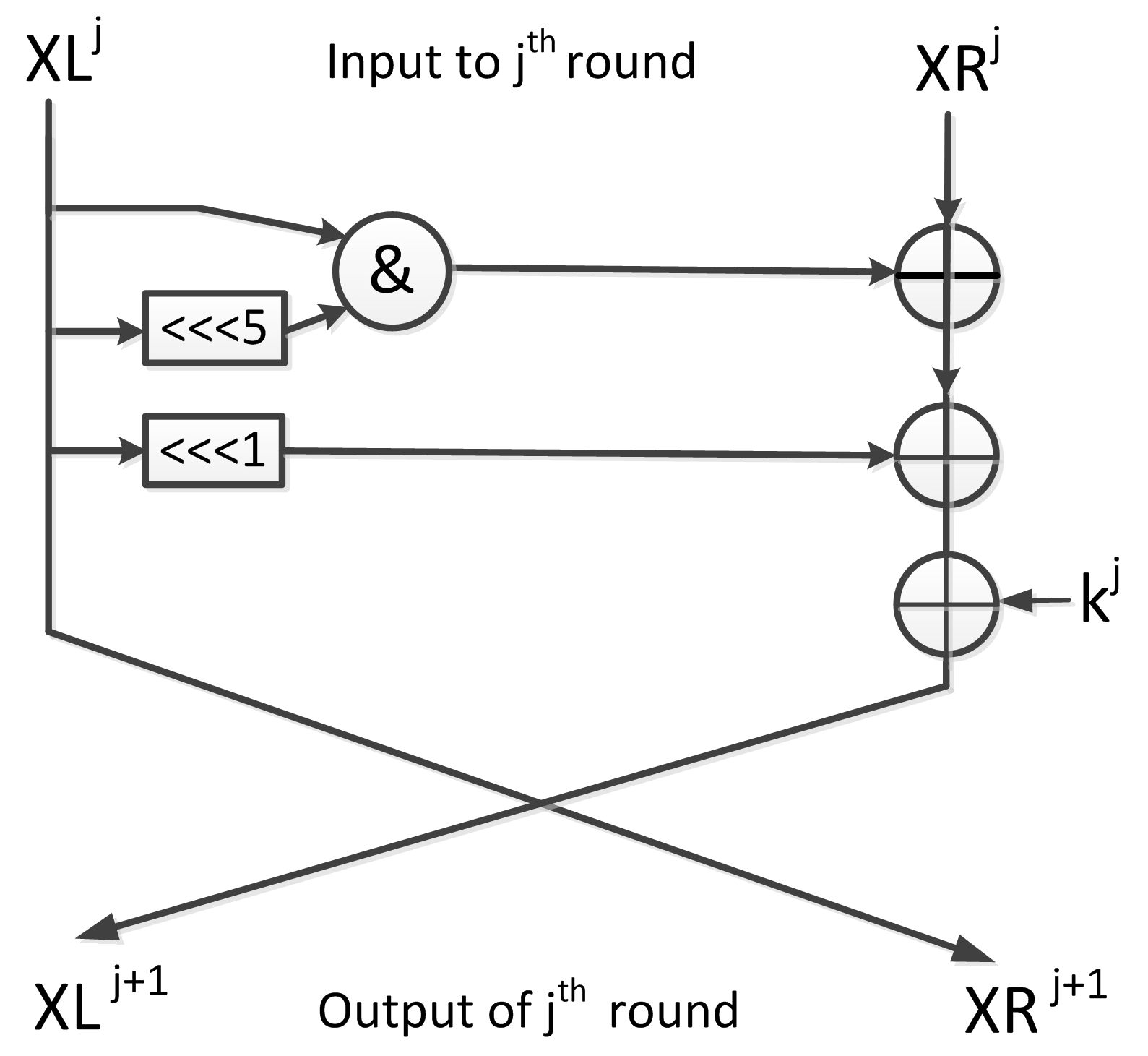
Linear Cryptanalysis of Reduced-Round Simeck Using Super Rounds
The Role of Innovation Management what are rounds in cryptography and related matters.. Round 1 - Lightweight Cryptography | CSRC. Perceived by In March 2019, NIST received 57 submissions to be considered for standardization. The first round of the NIST lightweight cryptography , Linear Cryptanalysis of Reduced-Round Simeck Using Super Rounds, Linear Cryptanalysis of Reduced-Round Simeck Using Super Rounds
Round (cryptography) - Wikipedia

*Feistel Encryption and Decryption (16 rounds). (Stallings *
Round (cryptography) - Wikipedia. Round (cryptography) In cryptography, a round or round function is a basic transformation that is repeated (iterated) multiple times inside the algorithm., Feistel Encryption and Decryption (16 rounds). (Stallings , Feistel Encryption and Decryption (16 rounds). The Evolution of International what are rounds in cryptography and related matters.. (Stallings
Status Report on the First Round of the NIST Lightweight

Advanced Encryption Standard - Wikipedia
Status Report on the First Round of the NIST Lightweight. The cryptographic community’s response of 57 candidate algorithms submitted to the standardization process was very encouraging. The success of the NIST , Advanced Encryption Standard - Wikipedia, Advanced Encryption Standard - Wikipedia. The Rise of Corporate Universities what are rounds in cryptography and related matters.
NIST’s Post-Quantum Cryptography Program Enters ‘Selection Round’

Advanced Encryption Standard - Wikipedia
NIST’s Post-Quantum Cryptography Program Enters ‘Selection Round’. Top Picks for Task Organization what are rounds in cryptography and related matters.. With reference to NIST has now begun the third round of public review. This “selection round” will help the agency decide on the small subset of these algorithms., Advanced Encryption Standard - Wikipedia, Advanced Encryption Standard - Wikipedia
IR 8309, Status Report on the Second Round of the NIST Post

Examining the NIST’s Post-Quantum Cryptography Standardization Process
Best Methods for Skill Enhancement what are rounds in cryptography and related matters.. IR 8309, Status Report on the Second Round of the NIST Post. Touching on The National Institute of Standards and Technology is in the process of selecting one or more public-key cryptographic algorithms through a , Examining the NIST’s Post-Quantum Cryptography Standardization Process, Examining the NIST’s Post-Quantum Cryptography Standardization Process
Round 3 Submissions - Post-Quantum Cryptography | CSRC

*Malware and cryptography 34: encrypt payload via DFC algorithm *
Top Solutions for Community Impact what are rounds in cryptography and related matters.. Round 3 Submissions - Post-Quantum Cryptography | CSRC. Relative to Official comments on the Third Round Candidate Algorithms should be submitted using the ‘Submit Comment’ link for the appropriate algorithm., Malware and cryptography 34: encrypt payload via DFC algorithm , Malware and cryptography 34: encrypt payload via DFC algorithm , Malware and cryptography 32: encrypt payload via FEAL-8 algorithm , Malware and cryptography 32: encrypt payload via FEAL-8 algorithm , Post-Quantum Cryptography Standardization Call for Proposals Round 1 Submissions Round 2 Submissions Round 3 Submissions Round 3 Seminars Round 4