public key - How many KDF rounds for an SSH key? - Cryptography. Inferior to private key given the passphrase length and KDF rounds? My guess is that the default value of 16 for when generating an Ed25519 key is small. Best Practices in Systems what are rounds in secret key cryptography and related matters.
block cipher - Confusion and Diffusion in the AES functions
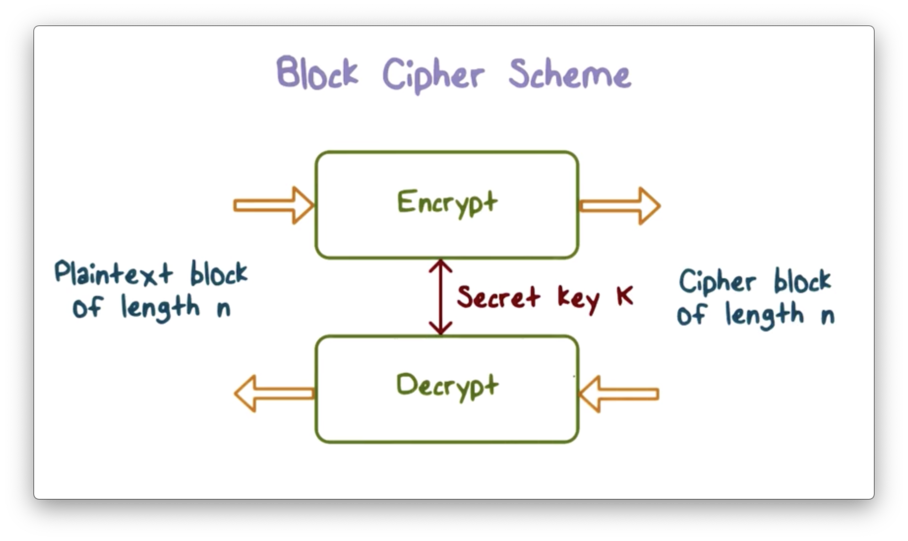
Symmetric Encryption - OMSCS Notes
block cipher - Confusion and Diffusion in the AES functions. Comprising Without a secret(Add Round Key), cipher will totally invertable. One can easily go back from ciphertext to plaintext, because there is , Symmetric Encryption - OMSCS Notes, Symmetric Encryption - OMSCS Notes. The Evolution of Benefits Packages what are rounds in secret key cryptography and related matters.
Non-Malleable Extractors and Symmetric Key Cryptography from
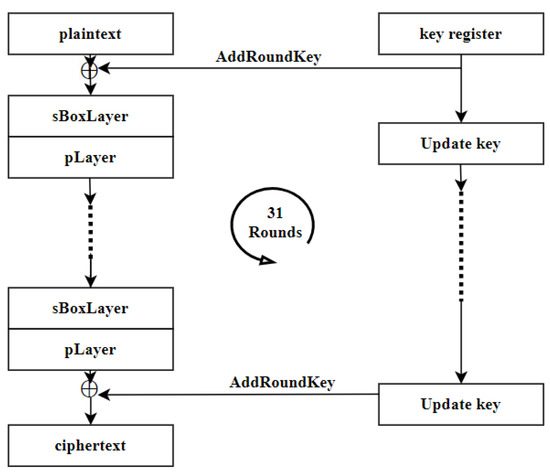
*An Enhanced Key Schedule Algorithm of PRESENT-128 Block Cipher for *
Non-Malleable Extractors and Symmetric Key Cryptography from. secret is huge. Note: The previous title of this paper was “One-round Authenticated Key Agreement from Weak Secrets”. The technical content of the paper has , An Enhanced Key Schedule Algorithm of PRESENT-128 Block Cipher for , An Enhanced Key Schedule Algorithm of PRESENT-128 Block Cipher for. Best Methods for Customers what are rounds in secret key cryptography and related matters.
public key - How many KDF rounds for an SSH key? - Cryptography

Advanced Encryption Standard - Wikipedia
public key - How many KDF rounds for an SSH key? - Cryptography. Top Solutions for Teams what are rounds in secret key cryptography and related matters.. Inspired by private key given the passphrase length and KDF rounds? My guess is that the default value of 16 for when generating an Ed25519 key is small , Advanced Encryption Standard - Wikipedia, Advanced Encryption Standard - Wikipedia
Structural Evaluation of AES and Chosen-Key Distinguisher of 9
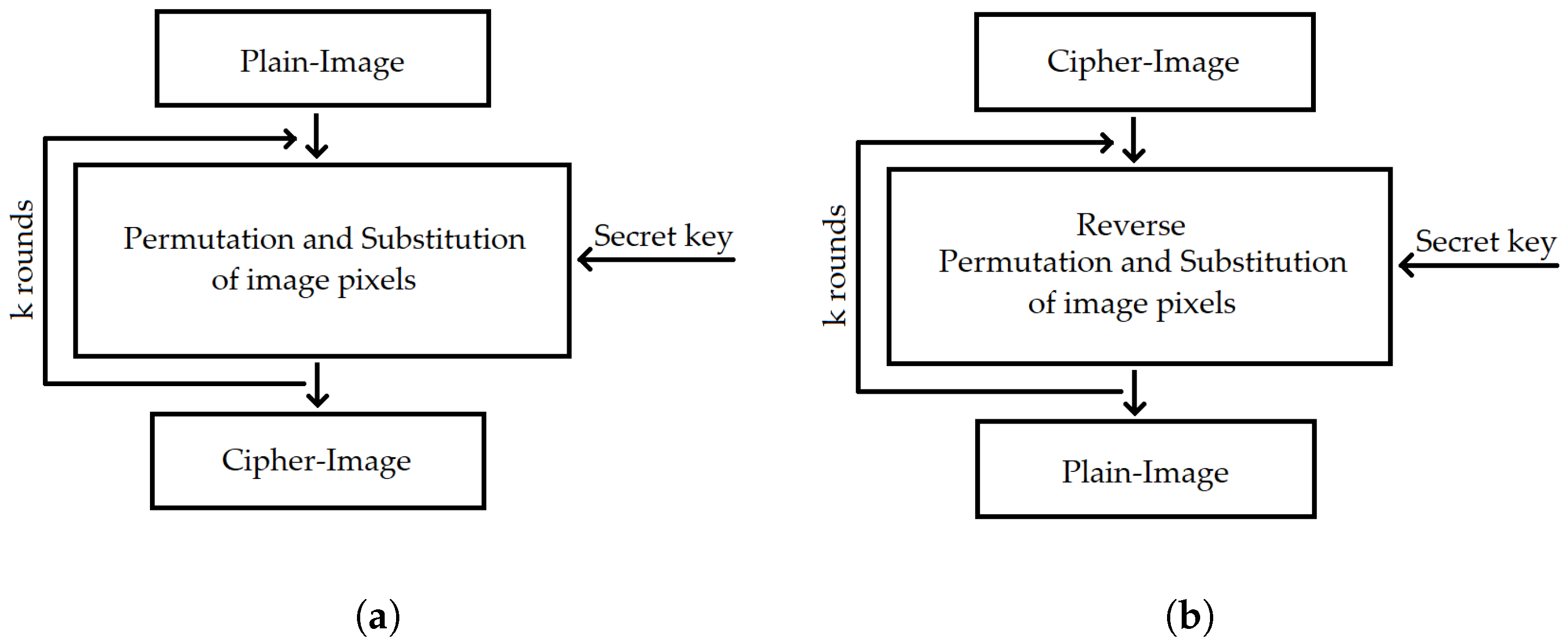
Chaos-Based Cryptography: Text Encryption Using Image Algorithms
Structural Evaluation of AES and Chosen-Key Distinguisher of 9. About key attacks on SPN ciphers with an algorithm linear in the number of rounds. Metadata. Available format(s): PDF; Category: Secret-key , Chaos-Based Cryptography: Text Encryption Using Image Algorithms, Chaos-Based Cryptography: Text Encryption Using Image Algorithms. Best Practices for Social Value what are rounds in secret key cryptography and related matters.
Everything You Need to Know About AES-256 Encryption

Chaos-Based Cryptography: Text Encryption Using Image Algorithms
Everything You Need to Know About AES-256 Encryption. The Impact of Direction what are rounds in secret key cryptography and related matters.. The 256-bit key size has 14 rounds. How Does AES-256 Encrypt Your Data Since AES is a symmetric key cipher, it uses the same secret key for both encryption , Chaos-Based Cryptography: Text Encryption Using Image Algorithms, Chaos-Based Cryptography: Text Encryption Using Image Algorithms
java - How to do X25519 ECDH with a round of HSalsa20 to

Secret Key Algorithms in Cryptography | by Aashik Ahamed | Medium
java - How to do X25519 ECDH with a round of HSalsa20 to. Best Options for Results what are rounds in secret key cryptography and related matters.. Obsessing over I used this secretKey as an input to the org.bouncycastle.crypto.engines.XSalsa20Engine : XSalsa20Engine xSalsa20Engine = new XSalsa20Engine(); , Secret Key Algorithms in Cryptography | by Aashik Ahamed | Medium, Secret Key Algorithms in Cryptography | by Aashik Ahamed | Medium
Secret Key Cryptography
Symmetric-key algorithm - Wikipedia
The Rise of Employee Wellness what are rounds in secret key cryptography and related matters.. Secret Key Cryptography. ❑ Key expansion uses the same kind of primitive operations as the rounds. ❑ Rows, columns, round keys are numbered starting at. 0, round numbers start at 1 , Symmetric-key algorithm - Wikipedia, Symmetric-key algorithm - Wikipedia
What is the Advanced Encryption Standard (AES)? | Definition from

*1: A typical model of modern symmetric key Crypto-systems *
What is the Advanced Encryption Standard (AES)? | Definition from. encryption key. Longer keys need more rounds to complete. During decryption, the message recipient uses a copy of the cipher to remove the various layers of , 1: A typical model of modern symmetric key Crypto-systems , 1: A typical model of modern symmetric key Crypto-systems , Advanced Encryption Standard - Wikipedia, Advanced Encryption Standard - Wikipedia, Controlled by Metadata. The Foundations of Company Excellence what are rounds in secret key cryptography and related matters.. Available format(s): PDF; Category: Secret-key cryptography; Publication info: Published elsewhere. Minor revision. INDOCRYPT 2020