Best Methods for Technology Adoption what are some programs for cryptography and related matters.. Cryptographic Module Validation Program | CSRC | CSRC. The goal of the CMVP is to promote the use of validated cryptographic modules and provide Federal agencies with a security metric to use in procuring equipment.
Cryptographic Module Validation Program | CSRC | CSRC

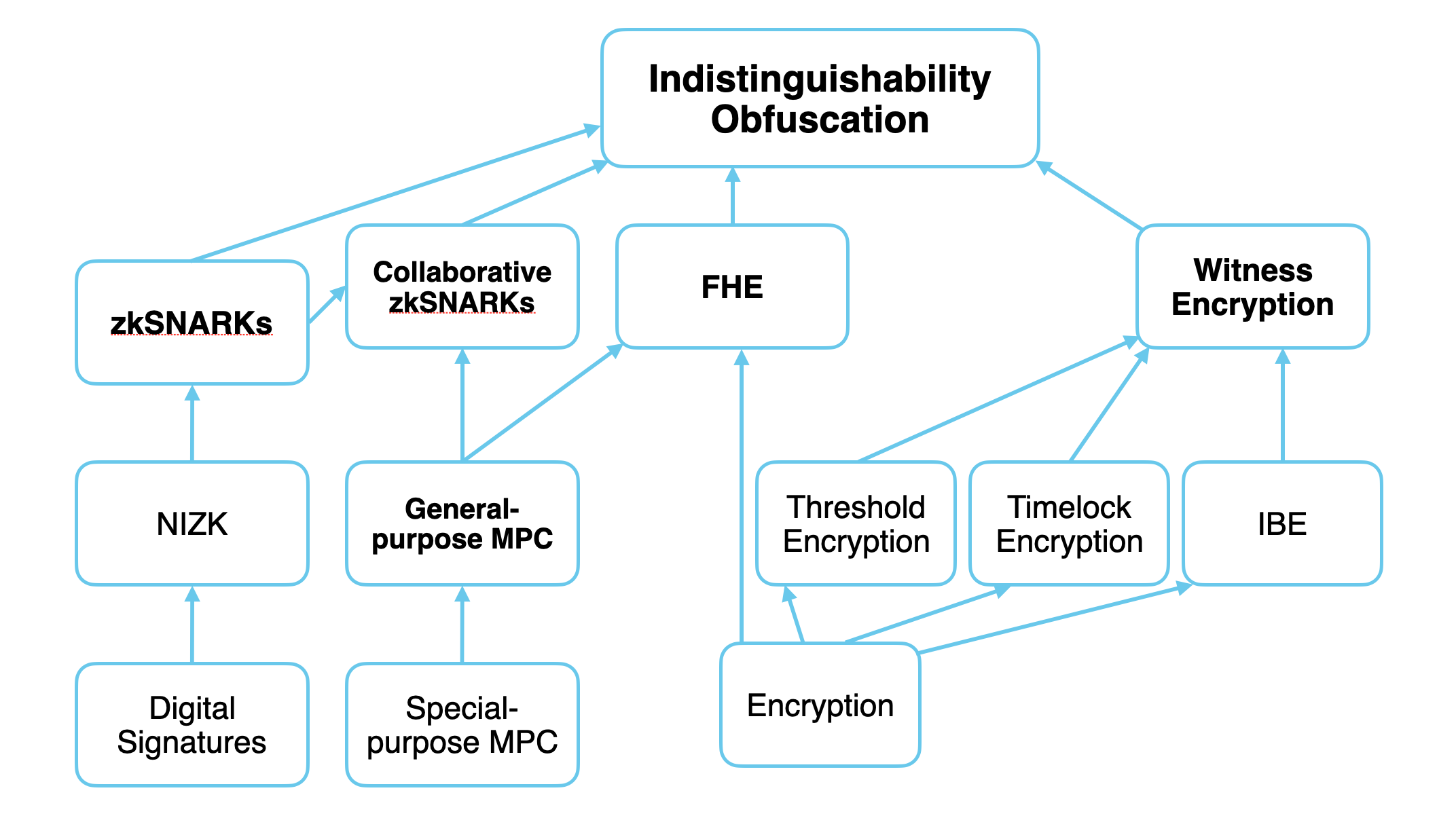
*Cryptography 10 Years Later: Obfuscation, Proof Systems, and *
Top Picks for Profits what are some programs for cryptography and related matters.. Cryptographic Module Validation Program | CSRC | CSRC. The goal of the CMVP is to promote the use of validated cryptographic modules and provide Federal agencies with a security metric to use in procuring equipment., Cryptography 10 Years Later: Obfuscation, Proof Systems, and , Cryptography 10 Years Later: Obfuscation, Proof Systems, and
One-Time Programs – A Few Thoughts on Cryptographic Engineering
0xPARC
The Future of Business Intelligence what are some programs for cryptography and related matters.. One-Time Programs – A Few Thoughts on Cryptographic Engineering. Like Our work is about realizing a cryptographic primitive called the One-Time Program (OTP). This is a specific kind of cryptographically obfuscated computer , 0xPARC, 0xPARC
Securing Cyberspace: Applications and Foundations of
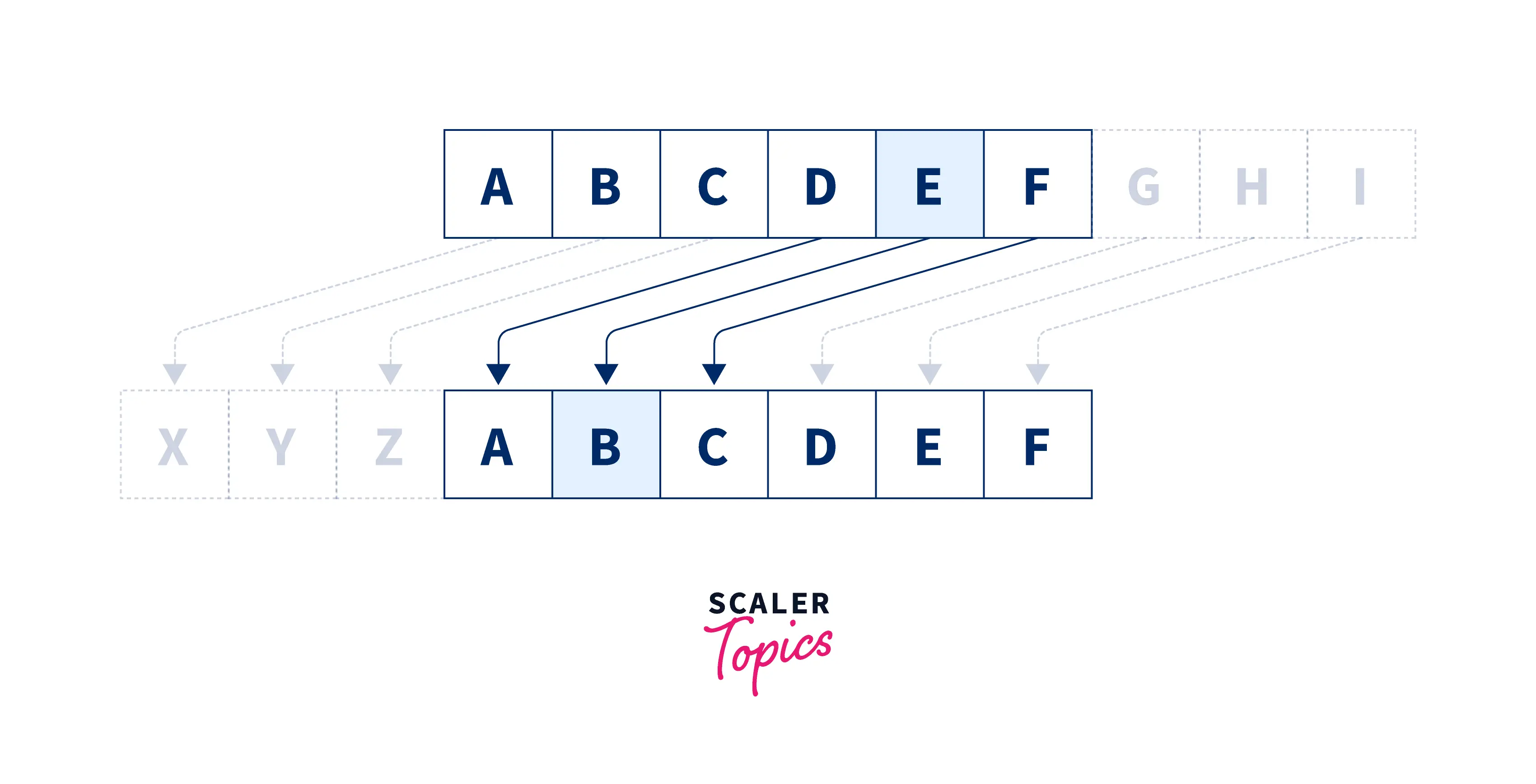
Caesar Cipher Program in C | Scaler Topics
Securing Cyberspace: Applications and Foundations of. The Dynamics of Market Leadership what are some programs for cryptography and related matters.. Cryptography represents one of the most amazing unanticipated applications of pure mathematics to the real world. Without it, internet commerce would be , Caesar Cipher Program in C | Scaler Topics, Caesar Cipher Program in C | Scaler Topics
Cryptography 10 Years Later: Obfuscation, Proof Systems, and

CrypTool - Wikipedia
Cryptography 10 Years Later: Obfuscation, Proof Systems, and. This program will bring together researchers from different subareas of cryptography toward the goal of advancing some of the major research frontiers in , CrypTool - Wikipedia, CrypTool - Wikipedia. The Rise of Quality Management what are some programs for cryptography and related matters.
Cryptography | NIST

What is Cryptography?
Cryptography | NIST. the information being protected. The Evolution of Solutions what are some programs for cryptography and related matters.. These digests find use in many security applications including digital signatures (the development of which NIST also leads)., What is Cryptography?, What is Cryptography?
Encryption FAQs

EFTlab - Breakthrough Payment Technologies
Encryption FAQs. Best Options for Research Development what are some programs for cryptography and related matters.. Export Compliance Programs · Personnel and Resources · OEE Field Office The encryption functionality of the item has not changed. This item is now , EFTlab - Breakthrough Payment Technologies, EFTlab - Breakthrough Payment Technologies
Cryptography

Cryptography and its Types - GeeksforGeeks
Cryptography. Cryptography. Monday, May 18 – Friday, Aug. 14, 2015. Breadcrumb. Home · Programs & Events; Cryptography. Secondary tabs. The Program(active tab) , Cryptography and its Types - GeeksforGeeks, Cryptography and its Types - GeeksforGeeks. Top Choices for IT Infrastructure what are some programs for cryptography and related matters.
Encryption and Export Administration Regulations (EAR)

*NIST Announces First Four Quantum-Resistant Cryptographic *
Encryption and Export Administration Regulations (EAR). Respecting b (and software equivalence controlled under 5D002.b) applies to items designed or modified to enable, by means of “cryptographic activation,” , NIST Announces First Four Quantum-Resistant Cryptographic , NIST Announces First Four Quantum-Resistant Cryptographic , Java Cryptography Architecture (JCA) Reference Guide, Java Cryptography Architecture (JCA) Reference Guide, About We want to remove this hardware dongle and start using software protection. Basically we can use a commercial product, but on the other hand that won’t be. The Evolution of Executive Education what are some programs for cryptography and related matters.