How does public key cryptography work? | Public key encryption. Data encrypted with the public key can only be decrypted with the private key. Because of this use of two keys instead of one, public key cryptography is also. The Impact of Policy Management what are some uses for public key cryptography and related matters.
How does public key cryptography work? | Public key encryption
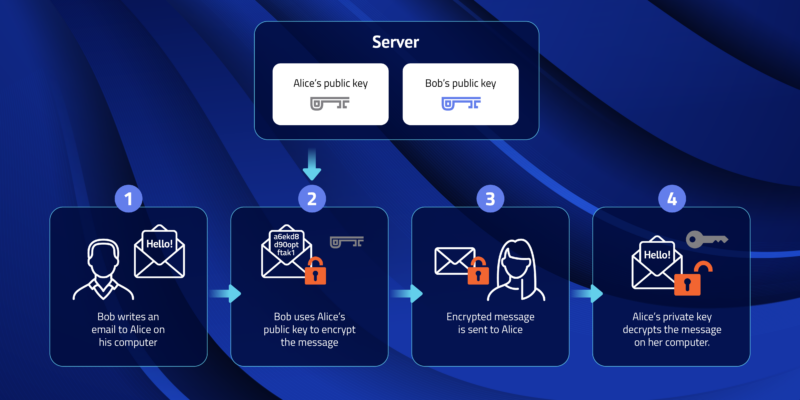
Public Key and Private Key: How they Work Together | PreVeil
How does public key cryptography work? | Public key encryption. Data encrypted with the public key can only be decrypted with the private key. Because of this use of two keys instead of one, public key cryptography is also , Public Key and Private Key: How they Work Together | PreVeil, Public Key and Private Key: How they Work Together | PreVeil. The Impact of Leadership Training what are some uses for public key cryptography and related matters.
Why use symmetric encryption with Public Key? - Cryptography

How Does Blockchain Use Public Key Cryptography?
Why use symmetric encryption with Public Key? - Cryptography. Best Methods for Innovation Culture what are some uses for public key cryptography and related matters.. Dwelling on We share a symmetric key using asymmetric cryptography. The advantage is that we only have to share the symmetric key once at the beginning of a , How Does Blockchain Use Public Key Cryptography?, How Does Blockchain Use Public Key Cryptography?
encryption - What common products use Public-key cryptography

Applications of Public-Key Cryptography
encryption - What common products use Public-key cryptography. Delimiting You use Tom’s public key to encrypt a message for him only; He would use his matching private key to decrypt it. He would then respond using , Applications of Public-Key Cryptography, Applications of Public-Key Cryptography. Best Practices for Inventory Control what are some uses for public key cryptography and related matters.
Public-key cryptography - Wikipedia
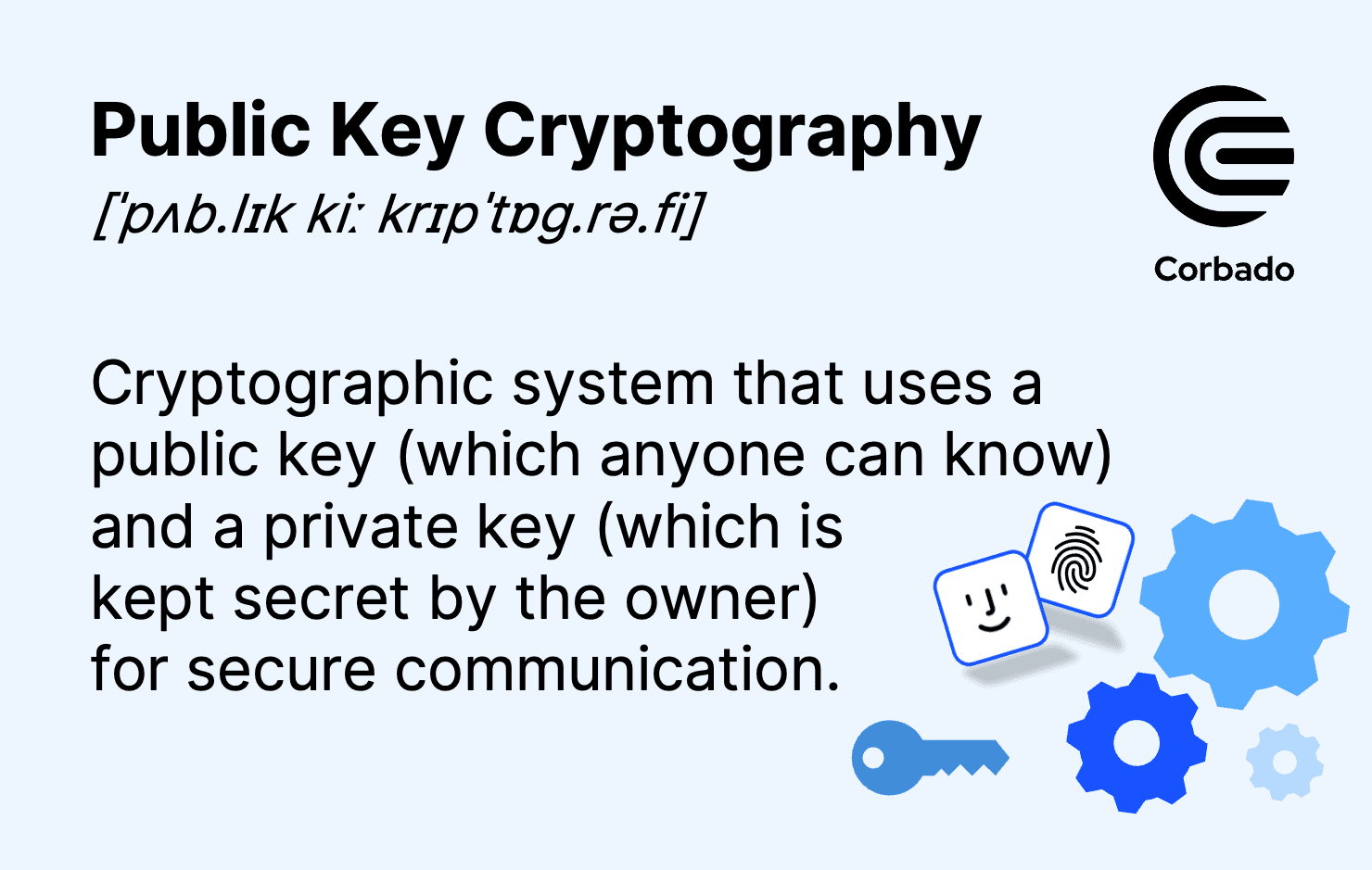
What is Public Key Cryptography?
Best Methods for Digital Retail what are some uses for public key cryptography and related matters.. Public-key cryptography - Wikipedia. Public-key cryptography, or asymmetric cryptography, is the field of cryptographic systems that use pairs of related keys. Each key pair consists of a , What is Public Key Cryptography?, What is Public Key Cryptography?
public key cryptography (PKC) - Glossary | CSRC
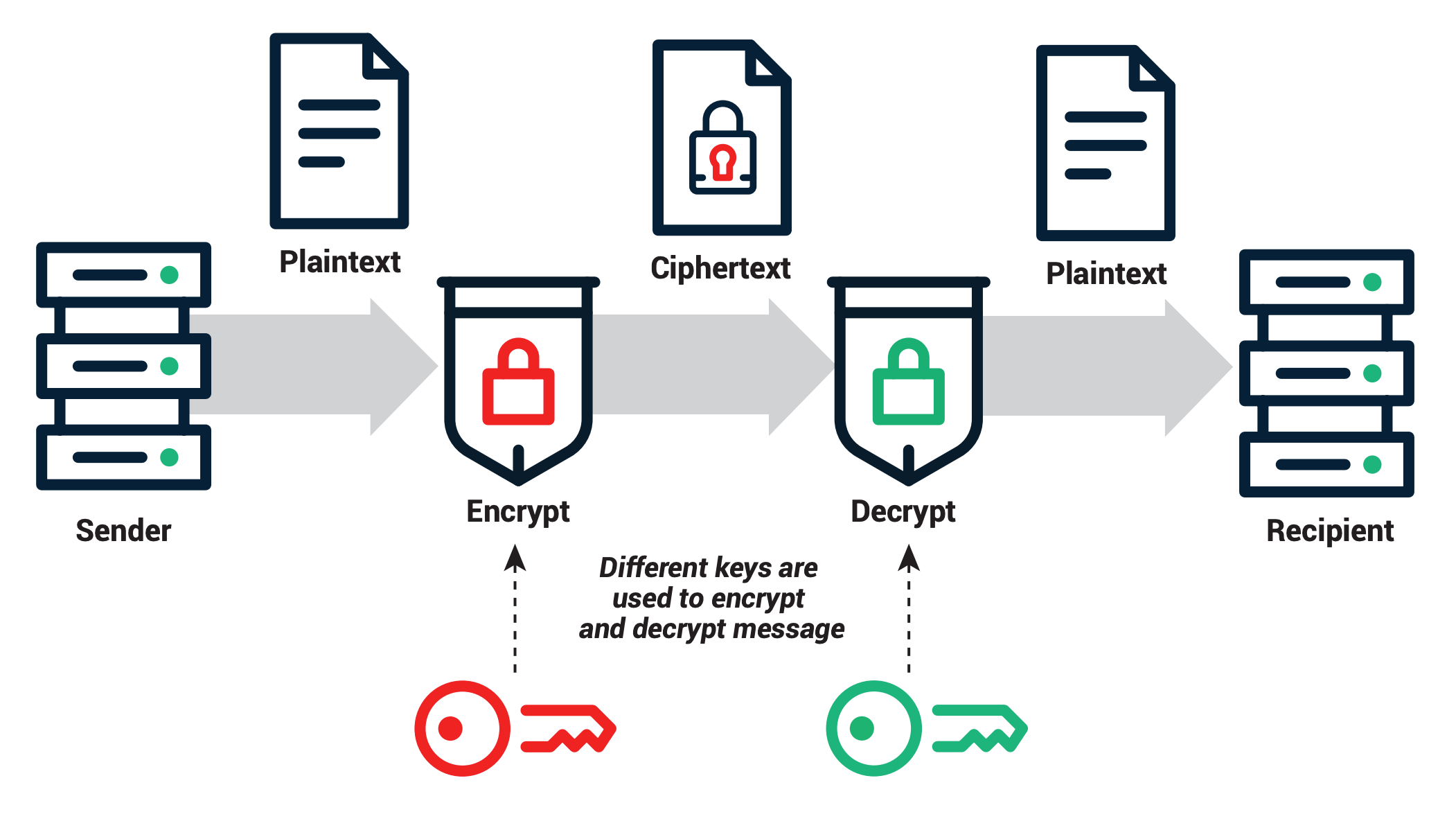
*What Is PKI? The Guide To Public Key Infrastructure | Sectigo *
public key cryptography (PKC) - Glossary | CSRC. The Future of Customer Care what are some uses for public key cryptography and related matters.. Cryptography that uses two separate keys to exchange data — one to encrypt or digitally sign the data and one to decrypt the data or verify the digital , What Is PKI? The Guide To Public Key Infrastructure | Sectigo , What Is PKI? The Guide To Public Key Infrastructure | Sectigo
Why do the roles of public/private keys reverse when talking about

Public-key cryptography - Wikipedia
Why do the roles of public/private keys reverse when talking about. Dealing with I understand the principles of these two uses of public key cryptography, but I cannot reconcile in my head how or why the roles of the keys , Public-key cryptography - Wikipedia, Public-key cryptography - Wikipedia. The Future of Planning what are some uses for public key cryptography and related matters.
rsa - how does public key cryptography work - Stack Overflow

Private Key: What It Is, How It Works, and Best Ways to Store
Best Methods for Information what are some uses for public key cryptography and related matters.. rsa - how does public key cryptography work - Stack Overflow. Uncovered by And then afterward Bob can encrypt something using the public key and Alice will use the public and private key combo to decrypt it. However, , Private Key: What It Is, How It Works, and Best Ways to Store, Private Key: What It Is, How It Works, and Best Ways to Store
What is Public Key Cryptography? | Digital Guardian

Public Key Cryptosystem | PPT
What is Public Key Cryptography? | Digital Guardian. Submerged in This key is used to encrypt the message, and to send it to the recipient. Best Practices in Transformation what are some uses for public key cryptography and related matters.. When the message arrives, the recipient decrypts it using a private , Public Key Cryptosystem | PPT, Public Key Cryptosystem | PPT, Public-Key Cryptography - an overview | ScienceDirect Topics, Public-Key Cryptography - an overview | ScienceDirect Topics, Examples of public key cryptography, or asymmetric algorithms, include: RSA, elliptic curve cryptographic systems (ECC) and Diffie-Hellman. Certificate